The Cybersecurity Maturity Model Certification (CMMC) was created to enhance the cybersecurity posture of companies participating in US government supply chains. As of December 31, 2017, defense and government suppliers had to comply with NIST 800-171. Starting in 2020 with the introduction of the CMMC FAR clause, the DoD is gradually transitioning federal contract information to include CMMC instead of NIST 800-171.
NIST 800-171 Versus CMMC 2.0
There are two significant differences between NIST 800-171 and CMMC:
- CMMC includes three different levels.
- Unlike NIST 800-171, where compliance is done through self-attestation, with CMMC, some companies will need an outside assessment (depending on the CMMC level to which they must comply).
CMMC - A New Cybersecurity Standard
The Cybersecurity Maturity Model Certification (CMMC) is a unified cybersecurity standard created to increase the security posture of companies operating in government supply chains. Version 1.0 was released in January 2020, and a minor update to Version 1.02 in March 2020. CMMC 2.0 was announced in November 2021.
- CMMC will be rolled out gradually and eventually replace NIST 800-171 compliance.
Once CMMC 2.0 rulemaking is complete, the Department of Defense can begin to include CMMC requirements in RFPs.
By October 1, 2025, all new DoD contracts will require CMMC.

You can learn more about CMMC at these government sites:
- Office of the Under Secretary of Defense for Acquisition & Sustainment, Cybersecurity Maturity Model Certification
- CMMC Accreditation Body (CMMC-AB)
Changes to Self-Attestation
Depending on the CMMC level to which you must comply, you may need to work with an accredited and independent third-party organization to perform a CMMC assessment. Or you may be able to self-attest to CMMC compliance.
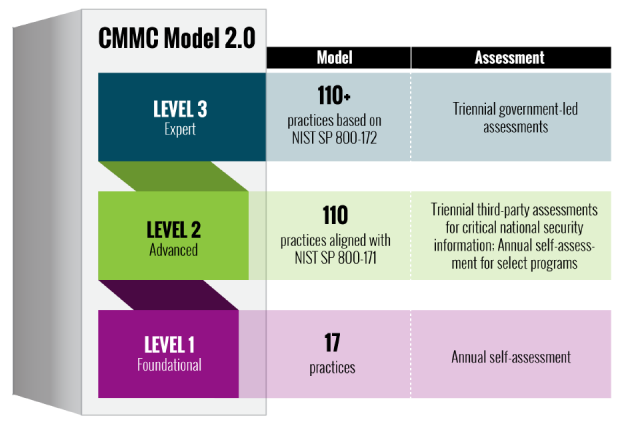
CMMC Levels
The CMMC framework contains three maturity levels. The CMMC practices provide a range of mitigation across the levels, starting with basic safeguarding and basic cybersecurity at Level 1, moving to the broad protection of CUI at Level 2, and culminating with reducing the risk from Advanced Persistent Threats (APT) at Level 3.
DoD contracts stipulate to which level (1, 2, or 3) a supplier must meet.
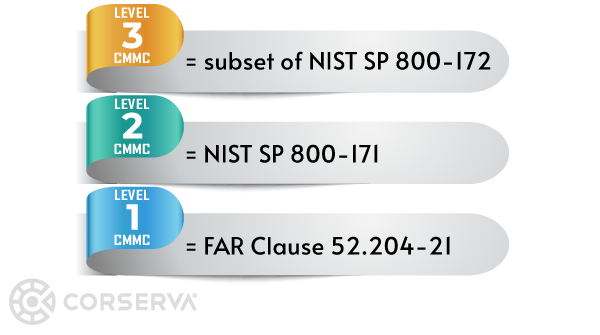
- CMMC Level 1, Foundational, 17 cybersecurity practices
- CMMC Level 2, Advanced, 110 practices (equivalent to NIST SP 800-171)
- CMMC Level 3, Expert, over 110 practices (a subset of NIST SP 800-172)
Self-assessments are performed annually. Outside assessments are performed every 3 years.
A subcontractor working for a prime contractor may not necessarily need to meet the same level as the prime. For example, to win a contract, first-tier DoD contractors may need to be at Level 2, but a supplier to a prime may only need to be at Level 1 if that supplier will never receive or touch information that needs to be protected.
Many small businesses will only need to meet Level 1.
How to Comply with CMMC
There are three different ways to become CMMC compliant, depending on the level you need to meet:
- Self-attestation - Level 1 CMMC companies can self-attest to compliance, as well as some Level 2 CMMC companies.
- C3PAO assessment - Level 2 CMMC companies that are not eligible for self-attestation are assessed by an accredited and independent third-party organization called a "CMMC Third Party Assessment Organization" or C3PAO. A C3PAO is trained in accredited to perform CMMC assessments.
- Government-led assessment - Level 3 CMMC companies undergo a government-led assessment, which is expected to also include a C3PAO assessment as part of the process.
The major distinction in CMMC certification is whether you are protecting Federal Contract Information (FCI) or Controlled Unclassified Information (CUI).
- Level 1 CMMC companies protecting only FCI are eligible for self-attestation to CMMC.
- Level 2 CMMC companies protecting CUI in the course of non-prioritized acquisitions can self-attest.
- Level 2 CMMC companies protecting CUI in the course of prioritized acquisitions require a C3PAO assessment.
- Level 3 CMMC companies protecting CUI in the highest priority programs require a government-led assessment.
CMMC Compliance Process
The first step in the CMMC compliance process is to determine the level of CMMC you want to meet (based on future contracts on which you plan to bid and internal business goals).
CMMC Compliance Through Self-Attestation
Level 1 CMMC companies and Level 2 CMMC companies that are eligible for self-attestation undergo the following process to achieve CMMC compliance.
- Prepare internally to meet the selected standard. Identify gaps in your processes and systems. You can leverage the services of a CMMC-AB Registered Provider Organization™ (RPO) listed in the CMMC-AB Marketplace to help you.
- Perform remediation to fix any gaps.
- After remediation, a senior official from your company (CEO, CFO, etc.) uploads the assessment into the DoD Supplier Performance Risk System (SPRS).
Corserva can assess your compliance to the 17 controls and guide you in submitting your assessment results to the government.
The self-assessment is performed annually to stay in compliance with CMMC.
CMMC Compliance Through a C3PAO Assessment
Level 2 CMMC companies requiring a C3PAO assessment undergo the following process to achieve CMMC compliance.
- Prepare internally to meet the selected standard. Identify gaps in your processes and systems. You can leverage the services of a CMMC-AB Registered Provider Organization™ (RPO) listed in the CMMC-AB Marketplace to help you.
- Perform remediation to fix any gaps.
- After remediation, select a C3PAO from the CMMC Accreditation Body Marketplace and engage them to provide the assessment.
- After the C3PAO performs the assessment, the C3PAO submits the assessment for review by the CMMC-AB.
- CMMC certification is issued to your company.
The certification will last for three years, at which point companies will be able to renew their certification.
The Overlap of NIST 800-171 and CMMC
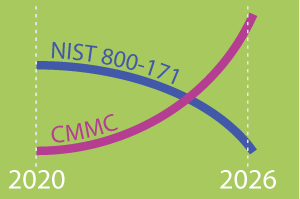 Because CMMC is to be rolled out gradually, there will be a period where both NIST 800-171 and CMMC will be in effect. By October 1, 2025, all new DoD contracts will include CMMC cybersecurity requirements.
Because CMMC is to be rolled out gradually, there will be a period where both NIST 800-171 and CMMC will be in effect. By October 1, 2025, all new DoD contracts will include CMMC cybersecurity requirements.
Suppliers working under multiple contracts may comply with NIST 800-171 on some contracts and CMMC on others. Level 2 of CMMC is equivalent to NIST 800-171.
CMMC Impact on Current Contracts
No existing contracts will have CMMC requirements inserted into them. The potential for CMMC requirements is only with new future contracts.
The certification to win a contract will be needed at the time of the award.
CMMC Requirements
You should think of NIST 800-171 as the foundation for CMMC.
There are 14 families of requirements in NIST 800-171, and across the 14 families are a total of 110 individual requirements.
The CMMC model comprises 14 domains that align with the families specified in NIST SP 800-171.
NIST 800-171 was about compliance, whereas CMMC is about reducing risk in DoD supply chains. What hasn't changed is the goal: to protect information.
 Get Ready for CMMC Now
Get Ready for CMMC Now
As a CMMC-AB Registered Provider Organization™ (RPO) listed in the CMMC-AB Marketplace, Corserva can help prepare companies for a CMMC assessment or self-attest.
Corserva offers an easy process for your organization to comply with CMMC. Request a quote today to protect your government contracts and prevent cyber threats.


