We are in the first year of the five-year rollout of the Cybersecurity Maturity Model Certification (CMMC) by the US Department of Defense. CMMC pilot programs are occurring, and Licensed Training Partners (LTP) are expected to begin offering training later in 2021 to Certified Assessors who will then perform CMMC assessments to Organizations Seeking Compliance (OSC). By 2026, all new DoD contracts will require compliance with CMMC.
If you are a US defense or government supplier or a subcontractor selling to a government supplier, you may need to meet CMMC on future contracts. The DoD is in the process of migrating from NIST 800-171 to the CMMC framework.
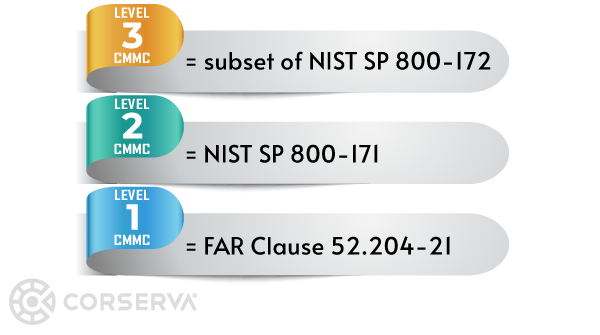
NIST 800-171 covers the protection of "Controlled Unclassified Information" (CUI), defined as information created by the government or an entity on behalf of the government that is unclassified but needs safeguarding.
NIST 800-171 provides guidelines that outline the processes and procedures companies need to implement to safeguard this information. NIST 800-171 provides guidance on how CUI should be accessed, shared, and stored securely.
Understanding the mandates leading up to the release of CMMC version 1.0 will better prepare you for your future CMMC assessments. If you are a company operating in DoD supply chains, working for a prime contractor or subcontractor, there are steps you should take now to protect your contracts.
FAR 52.204-21
On May 16, 2016, the government mandated that contractors protect their systems with the requisite 15 basic cybersecurity requirements, as described in FAR clause 52.204-21 Basic Safeguarding of Covered Contractor Information Systems.
What You Should Do Now— FAR 52.204-21
Read FAR clause 52.204-21 Basic Safeguarding of Covered Contractor Information Systems and make the changes needed to meet the 15 cybersecurity requirements.
DFARS 252.204-7012
The DFARS 252.204-7012 Safeguarding Covered Defense Information and Cyber Incident Reporting clause was published in October 2016 and directs compliance with NIST Special Publication 800-171. As of December 31, 2017, all contractors and subcontractors operating in government supply chains were expected to be compliant with NIST SP 800-171, which allowed for self-attestation.
The DFARS 252.204-7012 clause marked a major shift for the DoD by implementing 110 individual security requirements. Most importantly, contractors were required to document compliance and any gaps in security.
Requirements of 7012
The DFARS 252.204-7012 clause requires contractors and subcontractors to:
- Safeguard CUI by implementing cybersecurity requirements in NIST SP 800-171.
- Document in System Security Plans (SSP) how requirements are implemented.
- Maintain a Plan of Action with Milestones (POA&M) for requirements not yet implemented.
- Obtain approval from contracting officers for any variances or "alternate but equally effective controls" implemented to meet the requirements, as described in DFARS 252.204-7012(b)(2)(ii)(B).
- Report cyber incidents (including lost or stolen devices) to the DoD Cyber Crime Center (DC3).
- Isolate and submit malicious software for analysis to the DC3.
- Facilitate damage assessments.
- Flow down the clause to subcontractors if CUI is conveyed (not applicable to Commercial-Off-The-Shelf products).
What You Should Do Now— DFARS 252.204-7012
Read the DFARS 252.204-7012 Safeguarding Covered Defense Information and Cyber Incident Reporting clause and NIST SP 800-171. Perform an assessment to ensure you are meeting NIST 800-171. You can perform the assessment yourself (self-attestation), use an outside provider, or some combination.
DFARS 252.204-2012 is the foundation of CMMC.
CMMC Phases
CMMC is a unified cybersecurity standard created to increase the security posture of companies operating in government supply chains. The DoD is in the process of migrating from NIST 800-171 to the CMMC framework. CMMC is rolling out gradually and will eventually replace NIST 800-171 compliance. By 2026, all new DoD contracts will require CMMC.
Since the emergence of DFARS 252.204-7012 and NIST SP 800-171, three new regulations were introduced in November 2020, implementing a 5-year phased roll-out of CMMC.
- DFARS 252.204-7019
- DFARS 252.204-7020
- DFARS 252.204-7021
These have been described as the "crawl," "walk," and "run" phases of CMMC.
The newest DFARS regulations are enabling the DoD to verify that contractors who have attested to cybersecurity compliance are truly in compliance.
DFARS 252.204-7019
The DFARS 252.204-7019 Notice of NIST SP 800-171 DoD Assessments Requirements clause describes how if the contract under which you are working includes DFARS 252.204-7012, you must upload your assessment into the DoD Supplier Performance Risk System (SPRS).
Once you have uploaded your assessment into SPRS, you should begin working on closing any gaps identified in your assessment. Before you can pass a CMMC assessment, you will need to close any gaps, so you might as well get started on this work now so you are not scrambling later.
Requirements of 7019
The DFARS 252.204-7019 clause requires contractors and subcontractors to:
- Post a summary level score for their NIST SP 800-171 DoD assessment (Basic, Medium, or High) into the DoD’s SPRS for the applicable CAGE code and Systems Security Plan. The Basic assessment includes all 110 requirements of NIST 800-171.
- The summary level score must remain current (not older than three years unless a shorter time is specified) throughout the life of the contract, task, or delivery order.
What You Should Do Now— DFARS 252.204-7019
Read the DFARS 252.204-7019 Notice of NIST SP 800-171 DoD Assessments Requirements clause. Upload your assessment into SPRS, which should be at least a Basic assessment. Renew your assessment every three years at a minimum. Work to close any gaps you have.
DFARS 252.204-7020
The DFARS 252-204-7020 NIST SP 800-171 DoD Assessment Requirements clause describes how if the contract under which you are working includes DFARS 252.204-7012, the government has the right to audit your company to verify your compliance. You must also verify that any of your subcontractors who touch CUI have uploaded their assessment into SPRS.
The Defense Industrial Base Cybersecurity Assessment Center (DIBCAC) plans to perform approximately 100 audits per year, so you may or may not be audited. Over the next five years, as CMMC requirements are included in more contracts, the DIBCAC will gradually phase out.
Requirements of 7020
With the DFARS 252.204-7020 clause:
- A Basic Assessment Score is required in SPRS to be considered for contract award.
- Applicable to companies subject to DFARS clause 252.204-7012.
- Post-award, if the DoD deems a Medium or High assessment is necessary due to program sensitivity, you must provide the DoD access to your facilities, systems, and personnel.
- Include a clause in all subcontracts or other contractual instruments, including subcontracts for commercial items.
- Confirm subcontractor compliance with SPRS reporting if receiving CUI.
What You Should Do Now— DFARS 252.204-7020
Read the DFARS 252-204-7020 NIST SP 800-171 DoD Assessment Requirements clause. Determine which of your subcontractors touch CUI.
DFARS 252.204-7021
The DFARS 252-204.7021 Cybersecurity Maturity Model Certification Requirement clause describes how the government has until October 2025 to include CMMC requirements in all contracts, except those for Commercial-Off-The-Shelf (COTS) products and micropurchases. Contracts will stipulate to which level of CMMC you need to comply. This marks the end of POA&Ms.
Requirements of 7021
With the DFARS 252.204-7021 clause:
- Effective October 1, 2025, CMMC is required by contract award.
- Prior to October 1, 2025, the Office of the Undersecretary of Defense for Acquisition & Sustainment [OUSD(A&S)] must approve the inclusion of CMMC in new acquisitions.
- You must maintain the stipulated CMMC level of certification for the duration of the contract.
- The clause flows down — prime contractors must ensure that subcontractors are certified at the required CMMC level prior to awarding subcontract.
What You Should Do Now— DFARS 252.204-7021
Read the DFARS 252-204.7021 Cybersecurity Maturity Model Certification Requirement clause. Determine which level of CMMC you will need to meet on future contracts, based on past work and future business objectives.
Start researching potential assessors you could use to perform a future CMMC assessment. The CMMC Accreditation Body (CMMC-AB) Marketplace website is the sole authoritative source for entities authorized to perform CMMC assessments, Certified Third Party Assessment Organizations (C3PAO). Make sure any C3PAO you select has at least the Level 3 certification.
For more information describing how the regulatory requirements will be incorporated into new DoD acquisitions containing CUI beginning October 1, 2025, refer to Defense Federal Acquisition Regulation Supplement: Assessing Contractor Implementation of Cybersecurity Requirements.
What You Should Do Now to Get Ready for CMMC
- Perform a NIST 800-171 assessment (either with help from a third party or internally).
- Close the gaps on anything identified in your POA&M.
- Register in SPRS and upload your assessment summary.
- Get ready for DFAR 252-204.7021, when CMMC requirements will be included in all new federal contracts.
- Determine which CMMC level you will want.
- Prepare to self-certify to CMMC or for a future CMMC assessment.
What You Can't Do (Yet)
As of February 2021, you can't yet get a CMMC assessment.
Only C3PAOs identified in the CMMC-AB Marketplace are qualified to perform assessments. Training will begin in 2021 for C3PAOs after training programs and training exams have been finalized. Once C3PAOs have completed training, they will be able to start performing CMMC assessments.
An Easy Process to CMMC Compliance
As a CMMC-AB Registered Provider Organization™ (RPO), Corserva can advise companies in preparation for a CMMC assessment by a C3PAO.
Corserva offers an easy process for your organization to prepare for a CMMC assessment. Request a quote today to protect your government contracts and prevent cyber threats.




