When it comes to compliance, no one wants to overpay — for assessments, audits, tools, or services.
To be able to work under a federal contract that requires compliance with Cybersecurity Maturity Model Certification (CMMC), there is a good chance you will eventually need to pay for a CMMC assessment by a Certified 3rd Party Assessor Organization (C3PAO).
Various CMMC consulting services are available to better ensure your company will pass a CMMC assessment on the first try.
Not knowing what you should be doing is scary. Take steps now to prepare for a future CMMC assessment, so you don't waste money.
Reduce Your Costs for CMMC Compliance
Since the cost of a CMMC assessment is based on how you manage Controlled Unclassified Information (CUI) and not the size of your company, the best way to reduce your costs for a CMMC assessment is to narrow the scope of CUI.
This is how CMMC consulting services can save you money long term.
When preparing for your CMMC assessment, the following types of CMMC consulting services will reduce your costs for CMMC compliance.
- NIST assessments
- Creation of SSPs and POA&Ms
- CMMC readiness assessments
- Remediation of gaps and other issues
- Development of customized security programs to address gaps and issues
- Vulnerability scanning
- Implementation and configuration of compliant systems
- End-user training in cybersecurity best practices
1. NIST Assessments
Corserva performs NIST assessments for companies that need to comply with NIST Special Publication 800-171. The NIST 800-171 publication, and others like it created by NIST, have become recognized by IT security, compliance, and risk management professionals as a standard for best practice for any commercial enterprise. (This is why Corserva aligns its cybersecurity practice with the NIST cybersecurity framework.)
The DoD contract under which you are working determines whether you need to meet NIST 800-171 or CMMC.
The DFARS 252.204-7012 Safeguarding Covered Defense Information and Cyber Incident Reporting clause directs compliance with NIST SP 800-171. As of December 31, 2017, all contractors and subcontractors operating in government supply chains were expected to be compliant with NIST 800-171.
NIST Assessment Process
Corserva's NIST assessment process includes:
- Business process review
- Technical assessment of systems and networks
- Data analysis
During the assessment process, your information system environment as it relates to specific CUI cases will be reviewed. You will be asked about different access scenarios. Your policies and procedures regarding IT systems (formal, informal, and written) will also be reviewed.
For each of the 110 NIST 800-171 controls, Corserva will rate your company as fully compliant, partially compliant, or not compliant. We will provide you with supporting documentation on your compliance status and recommendations of what changes to make to become compliant in each area.
The NIST assessment process is as follows:
- Identify all relevant requirements within the NIST 800-171 Revision 2 security requirement families currently in effect.
- Perform an "as is" high-level assessment of the current state of processes and controls relative to the NIST 800-171 security requirements.
- Develop a gap analysis that identifies those areas where your processes and controls fall short of the NIST 800-171 security requirements.
- Develop a set of recommended actions you will need to take to align with the NIST 800-171 security requirements.
NIST Security Requirement Families
During project execution, Corserva performs an assessment of your compliance with the following NIST 800-171 security requirement families.
|
|
We then produce a report to reflect your compliance baseline. The report includes all data collected, your compliance status with each of the 110 controls, recommendations for remediation, and proposed next steps.
2. Creation of SSPs and POA&Ms
As evidence of NIST 800-171 compliance companies in the Defense Industrial Base develop and maintain formal documents for submission to DoD prime contractors upon contract initiation or renewal. These documents include a System Security Plan (SSP) and Plan of Action with Milestones (POA&M).
Nonfederal organizations describe, in a system security plan, how the security requirements are met or how organizations plan to meet the requirements and address known and anticipated threats. The system security plan describes: the system boundary; operational environment; how security requirements are implemented; and the relationships with or connections to other systems. Nonfederal organizations develop plans of action that describe how unimplemented security requirements will be met and how any planned mitigations will be implemented. Organizations can document the system security plan and the plan of action as separate or combined documents and in any chosen format.
The SSP and POA&M documents identify any gaps in compliance with NIST 800-171 and plan for how you will close the gaps.
Corserva can create your SSP and POA&M documents customized to your IT environment. These documents describe how any unimplemented security requirements will be met and how any planned improvements will be implemented. Detailed milestones are used to measure your progress.
After reviewing the documents with you, we will input the System Security Plan directly into the latest version of the published SSP template provided by NIST. The POA&M we create for you also follows the latest version of the POA&M template provided by NIST.
Using an SSP and POA&M as a Roadmap to CMMC Compliance
The SSP and POA&M are helpful to companies as they prepare to meet the more stringent requirements for CMMC. Until you close the gaps in compliance identified in an SSP and POA&M, you will not pass a CMMC audit.
If you have gone through the effort of creating an SSP and POA&M, you now have a roadmap of areas you will need to fix before a CMMC assessment.
As stipulated in Cybersecurity Maturity Model Certification (CMMC), you need to maintain system security plans to achieve CMMC compliance (depending on the CMMC level desired):
CA.L2-3.12.4 Develop, document, and periodically update system security plans that describe system boundaries, system environments of operation, how security requirements are implemented, and the relationships with or connections to other systems.
3. CMMC Readiness Assessments
For companies that need to comply with CMMC, Corserva can prepare you for a future CMMC assessment by performing an "assessment before the assessment" to determine your current compliance status.
CMMC Certification Levels
The CMMC framework contains three certification levels: Foundational, Advanced, and Expert.
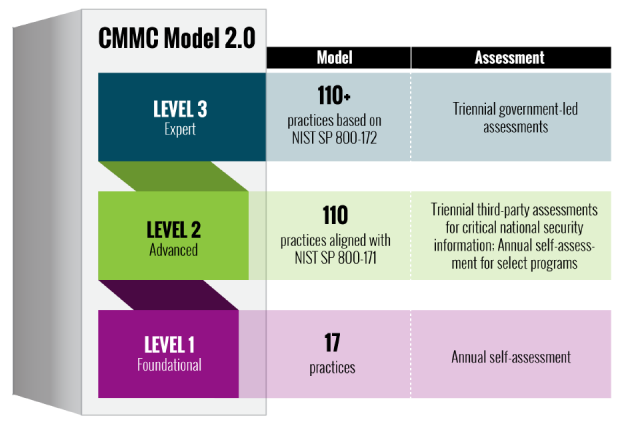
Prior to a CMMC assessment, you will first want to determine the level to which your company should be certified. This decision will be based on the contract under which you expect to work in the future or your internal business goals.
CMMC Readiness Assessment Process
This is the process Corserva follows when performing a CMMC readiness assessment:
- Identify all relevant requirements within the NIST 800-171 Revision 2 security requirement families and CMMC processes and practices for the desired level of compliance currently in effect (level 1, 2, or 3).
- Perform an "as is" high-level assessment of the current state of processes and controls relative to NIST 800-171 security requirements and CMMC processes and practices for your desired level.
- Develop a set of recommended actions you will need to take to align with the NIST 800-171 security requirements and CMMC processes and practices for the applicable level.
NIST Security Requirement Families & CMMC Domains
During project execution, Corserva performs an assessment of your compliance with the following NIST 800-171 security requirement families and CMMC capability domains.
The NIST 800-171 security requirement families are:
|
|
The CMMC model consists of 14 domains that align with the families specified in NIST SP 800-171.
After Corserva assesses your compliance with the NIST requirements and CMMC domains, we produce a report to reflect your compliance baseline. The report includes all data collected, your compliance status with the requirements of NIST 800-171 and the applicable level of CMMC, and recommendations for remediation and proposed next steps.
4. Remediation of Gaps and Other Issues
During a NIST assessment or CMMC readiness assessment, security gaps and other cybersecurity issues will be discovered.
If you have an SSP and POA&M, these documents can serve as a roadmap of areas that you will need to fix (at a minimum) before a formal CMMC assessment by a C3PAO.
With design or process changes, some of the systems you already have in place can be made compliant.
Corserva can remedy compliance gaps and issues by making configuration changes to:
- Firewalls
- Computers
- Servers
- Microsoft 365 and other platforms
- and more
As part of remediation efforts, Corserva can set up alerts to enable internal IT staff to proactively manage the IT infrastructure moving forward. You can also hire Corserva to monitor your IT infrastructure and make configuration changes as your infrastructure changes for ongoing compliance oversight.
5. Development of Customized Security Programs to Address Gaps and Issues
Your policies and procedures regarding IT systems (formal, informal, and written) will be reviewed during an assessment.
Where there are gaps in your written documentation, Corserva can create and document policies and procedures for you. We provide advice on best practices and can make any necessary configuration changes for you to support new policies and procedures.
For example, we can configure data access and sharing policies for email, OneDrive, SharePoint, etc.
6. Vulnerability Scanning
Depending on the level of CMMC compliance that applies to your company, you may need to meet the CMMC requirement for vulnerability scanning.
As stipulated in Cybersecurity Maturity Model Certification (CMMC), level 2 of the Risk Management domain:
RA.L2-3.11.2 Scan for vulnerabilities in organizational systems and applications periodically and when new vulnerabilities affecting those systems and applications are identified.
RA.L2-3.11.3 Remediate vulnerabilities in accordance with risk assessments.
Corserva can perform a baseline vulnerability scan, which includes:
- External scan of your IP addresses
- Agent deployment on test devices (both workstations and servers)
After the scan, Corserva creates a report to review with you, describing our findings and recommendations for remediation.
Corserva can also remediate issues identified during vulnerability scanning activities.
7. Implementation and Configuration of Compliant Systems
If you are planning to add any new platforms to help you meet CMMC compliance, it is important to remember that, in general, nothing is compliant right out of the box — the configuration is a big part of it.
For example, if you plan to implement Microsoft 365 GCC, Corserva can deploy a security configuration of the platform within your Microsoft Azure virtual server to align with compliance requirements.
If you are already using Microsoft 365 GCC, Corserva can review the current deployment of Microsoft 365 GCC to all endpoints and end users. Corserva will:
- Review and validate the deployed configuration of Microsoft 365.
- Validate access privileges and define user roles, then reconfigure where needed for compliance.
- Review and validate multi-factor authentication (MFA) settings and reconfigure where needed for compliance.
- Configure audit logging and alerting.
- Configure Azure Information Protection (AIP) for email encryption and document security.
- Configure data access and sharing policies for email, OneDrive, SharePoint, etc.
- Configure a sensitivity label to mark information as CUI for conditional access and DLP testing.
- Test and validate reconfigured features and services.
For Microsoft Azure, Corserva can:
- Configure non-privileged and privileged accounts.
- Configure secure remote access.
- Install and configure Microsoft Office applications and email.
- Provision the Outlook app for mobile device email access.
- Test and validate FIPS-validated disk encryption.
- Test and validate email, data access, logging, and reporting features and functionality.
Corserva also provides you with reference architecture diagrams and documentation.
After implementation, Corserva can provide training and support for new platforms.
8. End User Training in Cybersecurity Best Practices
CMMC compliance ensures that your employees have the required cybersecurity training. One of the 17 domains in CMMC is "Awareness and Training (AT)," which includes these capabilities:
- Conduct security awareness activities
- Conduct training
For those companies that are relatively new to CMMC, compliance often involves bringing a security-first mindset to the organization.
Corserva offers security awareness training and other cybersecurity training for your staff. We instruct employees in the latest mechanisms of spam, phishing, malware, ransomware, and social engineering so that they can apply this knowledge in their day-to-day activities, keeping the business protected from cyber threats.
Request a Quote for CMMC Consulting Services
 Corserva's CMMC consulting services prepare you for a CMMC assessment by a C3PAO, greatly reducing your costs and efforts to achieve CMMC compliance.
Corserva's CMMC consulting services prepare you for a CMMC assessment by a C3PAO, greatly reducing your costs and efforts to achieve CMMC compliance.
Corserva is a CMMC-AB Registered Provider Organization™ (RPO) and we are listed on the CMMC-AB Marketplace.
As an RPO, Corserva is authorized by the CMMC-AB to provide pre-assessment consulting services to government contractors.
Get started today. Talk to a CMMC compliance expert by requesting a quote for CMMC consulting.


