Since the Department of Defense revamped Cybersecurity Maturity Model Certification (CMMC) with the announcement of CMMC 2.0 on November 4, 2021, DoD contractors are left wondering if they will need CMMC certification.
The answer is still yes, but the way you might get there is changing.
What is CMMC certification?
CMMC is a unified cybersecurity standard for the implementation of cybersecurity across the Defense Industrial Base (DIB).
CMMC was created in response to lagging compliance with NIST Special Publication 800‑171, which required contractors working in government supply chains to comply as of December 31, 2017.
Because contractors could self-attest to compliance with NIST SP 800‑171, the DoD created CMMC to enhance national security and strengthen the cybersecurity of companies operating in government supply chains. The initial release of CMMC eliminated the option for self-attestation at any level. With the announcement of CMMC 2.0, self-attestation is an option for some companies at some levels.
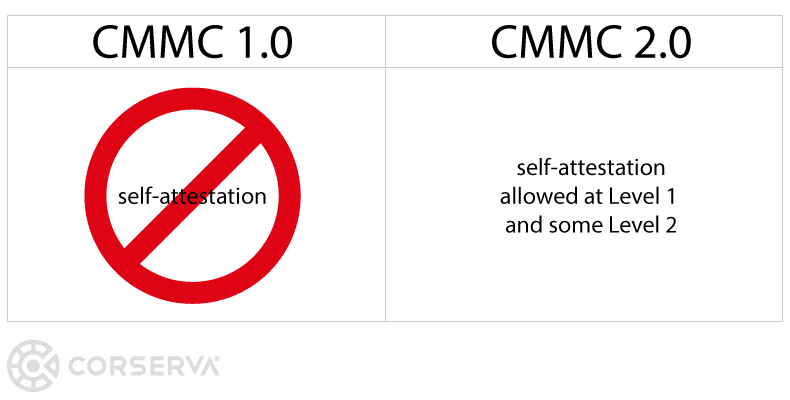
self-attestation is possible in some cases with the announcement of CMMC 2.0
CMMC Certification Applies to All Contractors
NIST 800-171 may have been the first exposure to compliance that many small companies working in government supply chains were faced with. As a flow-down clause, NIST 800-171 was the first compliance mandate that impacted not only prime contractors working directly for the government but also subcontractors working for primes or other subcontractors.
Like NIST 800-171, CMMC is also a flow-down clause. A company working under a government contract must comply with NIST 800-171 or CMMC (depending on the contract requirements) and ensure that every subcontractor working for them complies.
Companies performing under a DoD contract must maintain their CMMC certification throughout the contract.
Any entity in the government supply chain dealing with government-controlled unclassified information must be compliant. Typical entities include manufacturers, universities, research institutions, consulting companies, and service providers.
Companies that solely produce Commercial-Off-The-Shelf (COTS) products are not subject to CMMC requirements.
How to Get CMMC Certification
The method to become certified varies based on the level of CMMC you need to meet. The big distinction is whether you are protecting Federal Contract Information (FCI) or Controlled Unclassified Information (CUI).
- FCI is information not intended for public release that the US government provides under a contract to develop or deliver a product or service to the government, but not publicly available information, such as on websites.
- CUI is information the US government creates or possesses that a law, regulation, or government-side policy requires or permits an agency to handle using safeguarding or dissemination controls.
3 CMMC Levels
There are three levels in CMMC:
- Level 1 – Foundational
- Level 2 – Advanced
- Level 3 – Expert
The original CMMC framework had five levels, but that has changed since the announcement of CMMC 2.0.
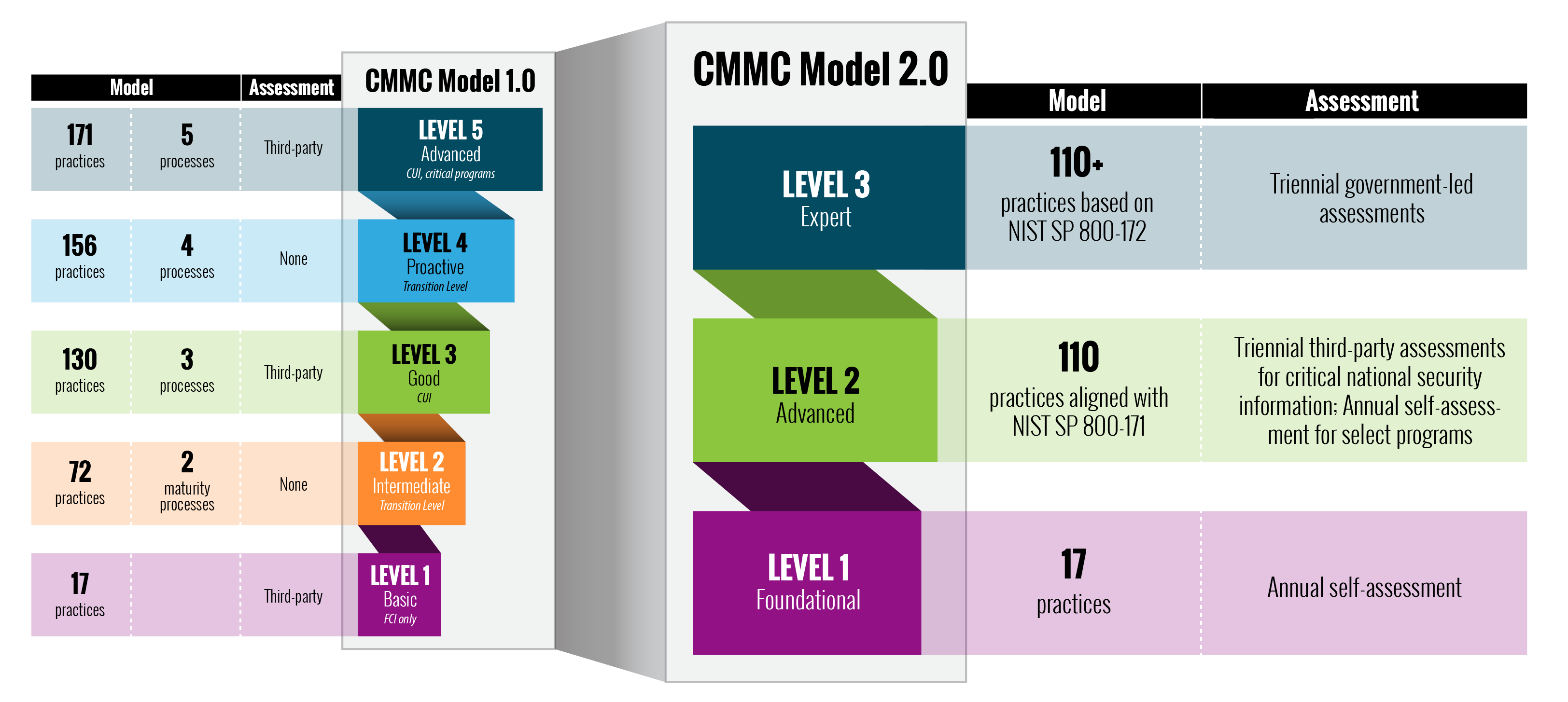
from Acquisition & Sustainment, Office of the Under Secretary of Defense
CMMC levels are based on the security criticality of the information you receive when performing under a contract. Level 2 compliance is harder to meet than Level 1 compliance, and Level 3 compliance is harder to meet than Level 2.
The contract under which you work will tell you which level you need to meet.
It is possible that you can be working for a prime contractor that has a higher level CMMC requirement than you do. If the prime only flows down select information, a lower CMMC level may apply to you.
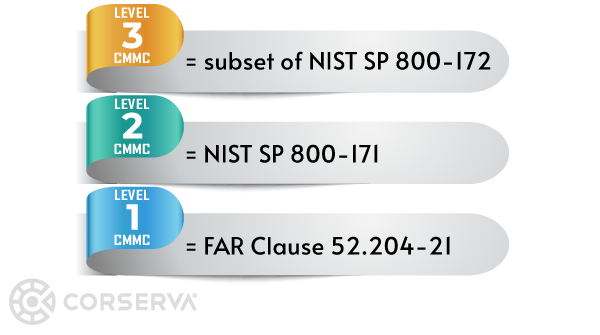
CMMC Level 1 – Foundational
To meet CMMC Level 1, you comply with 17 cybersecurity best practices.
- Domain: Access Control (AC), AC.L1-3.1.1 – Limit information system access to authorized users, processes acting on behalf of authorized users, or devices (including other information systems).
- Domain: Access Control (AC), AC.L1-3.1.2 – Limit information system access to the types of transactions and functions that authorized users are permitted to execute.
- Domain: Access Control (AC), AC.L1-3.1.20 – Verify and control/limit connections to and use of external information systems.
- Domain: Access Control (AC), AC.L1-3.1.22 – Control information posted or processed on publicly accessible information systems.
- Domain: Identification and Authentication (IA), IA.L1-3.5.1 – Identify information system users, processes acting on behalf of users, or devices.
- Domain: Identification and Authentication (IA), IA.L1-3.5.2 – Authenticate (or verify) the identities of those users, processes, or devices as a prerequisite to allowing access to organizational information systems.
- Domain: Media Protection (MP), MP.L1-3.8.3 – Sanitize or destroy information system media containing Federal Contract Information before disposal or release for reuse.
- Domain: Physical Protection (PE), PE.L1-3.10.1 – Limit physical access to organizational information systems, equipment, and the respective operating environments to authorized individuals.
- Domain: Physical Protection (PE), PE.L1-3.10.3 – Escort visitors and monitor visitor activity.
- Domain: Physical Protection (PE), PE.L1-3.10.4 – Maintain audit logs of physical access.
- Domain: Physical Protection (PE), PE.L1-3.10.5 – Control and manage physical access devices.
- Domain: System and Communications Protection (SC), SC.L1-3.13.1 – Monitor, control, and protect organizational communications (i.e., information transmitted or received by organizational information systems) at the external boundaries and key internal boundaries of the information systems.
- Domain: System and Communications Protection (SC), SC.L1-3.13.5 – Implement subnetworks for publicly accessible system components that are physically or logically separated from internal networks.
- Domain: System and Information Integrity (SI), SI.L1-3.14.1 – Identify, report, and correct information and information system flaws in a timely manner.
- Domain: System and Information Integrity (SI), SI.L1-3.14.2 – Provide protection from malicious code at appropriate locations within organizational information systems.
- Domain: System and Information Integrity (SI), SI.L1-3.14.4 – Update malicious code protection mechanisms when new releases are available.
- Domain: System and Information Integrity (SI), SI.L1-3.14.5 – Perform periodic scans of the information system and real-time scans of files from external sources as files are downloaded, opened, or executed.
Level 1 companies are protecting FCI, not CUI, and can self-certify. Many small businesses in the DIB will only need to meet Level 1 of CMMC.
To meet CMMC Level 1, you annually upload your assessment into the DoD Supplier Performance Risk System (SPRS). Only senior company officials (CEO, CFO, etc.) can make the CMMC Level 1 attestation to SPRS.
Corserva can assess your compliance with the 17 controls and guide you in submitting your assessment results to the government.
CMMC Level 2 – Advanced
To meet CMMC Level 2, you follow all 110 best practices identified in NIST SP 800-171.
A subset of Level 2 companies will be able to self-certify annually, and others will need to hire an outside assessor (C3PAO) to perform the assessment every three years.
Self-Certification
Companies that can self-certify will be able to use POA&Ms as an acceptable form of remediation for certain CMMC practices. POA&Ms will not be allowed for the highest-weighted requirements of CMMC.
You write POA&Ms (Plans of Actions with Milestones) to document controls to which you don't currently comply and how you plan to make changes to meet those gaps in the future.
Assuming you take the correct approach when developing a POA&M, it can be a valuable tool to improve the company's security posture. Just don't fall into the trap of using a POA&M as a checkmark to compliance. Instead of a procrastination step, your POA&M should be a roadmap to compliance, clearly outlining what steps you plan to take in the future to fully meet compliance.
In addition to POA&Ms, System Security Plans (SSP) can also be helpful on the path to a stronger security posture.
Corserva can create POA&Ms and SSPs for you and perform NIST 800-171 assessments.
C3PAO Assessments
A Certified 3rd Party Assessor Organization (C3PAO) is licensed by the CMMC Accreditation Body (CMMC-AB) to perform CMMC assessments. Only those companies listed as C3PAOs on the CMMC-AB Marketplace are authorized to perform C3PAO assessments.
Within the CMMC-AB Marketplace, note the distinction between an "Authorized C3PAO" and a "C3PAO Candidate." Only companies that are Authorized C3PAOs can perform CMMC assessments. A C3PAO Candidate has begun the process of applying to become a C3PAO but has not yet completed the process.
Level 2 companies requiring a C3PAO assessment can comply with CMMC as follows:
- Prepare for your CMMC assessment by performing a self-assessment or working with a partner. Corserva's CMMC expert advisors can help you with audit preparation.
- Visit the CMMC-AB Marketplace to research potential C3PAOs. Only C3PAOs listed on the CMMC-AB Marketplace are authorized by the CMMC-AB to perform assessments.
- Hire a C3PAO to perform a CMMC assessment for you.
- The C3PAO will create an assessment report and if there are no deficiencies, issue a CMMC certificate.
- The C3PAO will submit a copy of the assessment report and CMMC certificate to the DoD, which is valid for three years. This final step completes the requirement for CMMC compliance.
CMMC Level 3 – Expert
To meet CMMC Level 3, the company must meet more than 110 best practices based on NIST SP 800-172.
All Level 3 companies are required to pass a government-led assessment every three years.
When is CMMC certification required?
Entities that deal with government-controlled unclassified information must comply with NIST 800-171 or CMMC.
The DoD is gradually transitioning from the NIST 800-171 mandate to CMMC. Per DFARS 252.204-7021, all new DoD contracts must comply with CMMC by October 1, 2025. Before October 1, 2025, the CMMC clause can be included in new contracts when approved by the DoD.
In Requests for Information (RFI) and Requests for Proposals (RFP), the DoD will specify the required CMMC level to which you need to meet. You need to be certified before contract award.

What you Should Do Now to Prepare for CMMC
Follow these steps to prepare your company to participate in future government contracts that include CMMC requirements.
- Evaluate any current government contracts under which you are working to determine the level of certification you would need to meet in a future contract. Your federal officer, prime contractor, or subcontractor under which you work can provide guidance here.
- At a minimum, you will need to meet Level 1 of CMMC. Corserva can help you evaluate your compliance with the 17 controls.
- If you are handling CUI, look for ways to limit the amount of CUI you receive in fulfillment of a contract. Try to restrict the CUI you receive to only the data required for you to do your work. The less CUI you have, the easier it will be to protect it.
- Read NIST SP 800-171 to determine where your company falls short in cybersecurity best practices. Corserva can perform a NIST assessment to identify gaps in compliance.
- Perform remediation to close any gaps. You can do this yourself or work with a third-party provider such as Corserva to help you.
Corserva CMMC Compliance Services
 Corserva is a CMMC-AB Registered Provider Organization™ (RPO), and we are listed on the CMMC-AB Marketplace. As an RPO, Corserva is authorized by the CMMC-AB to provide pre-assessment consulting services to government contractors.
Corserva is a CMMC-AB Registered Provider Organization™ (RPO), and we are listed on the CMMC-AB Marketplace. As an RPO, Corserva is authorized by the CMMC-AB to provide pre-assessment consulting services to government contractors.
Corserva has created an easy process to help you get certified to CMMC at any level.
Corserva offers:
- Pre-assessment readiness services for CMMC
- Technical remediation to correct gaps in compliance
- Assessments for NIST 800-171
- Customized cybersecurity and compliance programs
Get started today by requesting a quote for CMMC consulting services.


