Now that the deadline to comply with the NIST 800-171 mandate has passed (as of December 31, 2017), hopefully you are sitting back, comfortable in the knowledge that you have taken the necessary steps to ensure your company is meeting the cybersecurity guidelines required by the Department of Defense (DoD), providing you a competitive advantage over other manufacturers.
If not, you may be starting to wonder...now what? What's going to happen? Am I too late?
3 Myths About NIST 800-171 and NIST Compliance
- "Becoming NIST compliant will cost us tens of thousands of dollars."
- "We're too small for NIST compliance."
- "It's too late for us to become NIST compliant."
Is it too late?
There are ramifications for non-compliance, but no, it's not too late to start down the path to becoming NIST compliant. In fact, you can realize advantages to becoming compliant with the NIST 800-171 mandate whenever you achieve compliance.
The NIST 800-171 Mandate
If you are a defense or government supplier – or if you are a subcontractor selling to a government supplier – you need to take steps to assess and comply with the NIST 800-171 mandate.
NIST is the National Institute of Standards and Technology. NIST Special Publication 800-171 covers the protection of "Controlled Unclassified Information" defined as information created by the government, or an entity on behalf of the government, that is unclassified, but needs safeguarding. The NIST 800-171 mandate provides a set of guidelines that outline the processes and procedures that companies need to implement to safeguard this information.
Who needs to comply?
You might be wondering, does NIST compliance really apply to my organization? Especially if you never received any formal notification (of that you are aware) from your prime contractor requiring you to do so. Ask yourself, does your company conduct business directly, or indirectly as a tiered supplier, with the US federal government or DoD?
Some organizations will receive direct notification about their need to comply. If you are a manufacturer, you may have been notified by a prime contractor or subcontractor stating that you need to comply with NIST 800-171. Notification can come directly via mail or email. Alternately, you might be notified when logging into a portal that you use for procurement or order management.
Keep in mind that if you receive no notification, this does not mean you do not need to comply with NIST 800-171.
It’s possible the notification was sent but the correct person to receive it never saw it. Corserva has worked with many manufacturers who never received formal notification to comply.
Depending on the federal contract under which you are working, you may need to comply with Cybersecurity Maturity Model Certification (CMMC).
Ramifications for Non-Compliance
As described in Defense Federal Acquisition Regulation Supplement (DFARS) 252.204-7012, “Safeguarding Covered Defense Information and Cyber Incident Reporting,” all DoD contractors (including small businesses) must meet the mandatory cybersecurity DFARS compliance as of December 31, 2017.
If a contractor does not have proof of compliance, the company risks removal from the approved DoD vendor list. The DoD Chief Information Officer must now be notified within 30 days of contract award of any security requirements not implemented at the time including cybersecurity compliance.
Don't risk loss of business. Getting started now will go a long way towards meeting compliance.
Areas of NIST
NIST 800-171 is broken out into 14 different families. For convenience, these families can be summarized into four main areas:
- Controls
- Monitoring & management
- End user practices
- Security measures
Entities that deal with government CUI should be compliant with NIST 800-171 as of December 31, 2017. Typical entities affected include universities, research institutions, consulting companies, service providers, and manufacturers.
Manufacturing companies that are prime contractors, or sub for prime contractors, that have CUI within their systems and applications will be impacted by this mandate. But there is a lot of inaccurate information floating around about NIST.
Myth #1
"Becoming NIST compliant will cost us tens of thousands of dollars."
No – don’t get ripped off. Affordable plans for becoming NIST compliant are available. Don’t assume you need the services of a very large consulting company, where you might pay tens of thousands of dollars, to become NIST compliant. Also, be wary of unscrupulous vendors who may use scare tactics in an effort to make you sign up with them without properly researching reputable vendors first.
There are costs involved in becoming NIST compliant, but you may not need to spend as much as you think.
Myth #2
"We don't work with the government, so we don't need to comply with NIST."
Not true. If you are in the federal supply chain, there is a high probability that you need to be compliant with the NIST 800-171 mandate. As stated above, NIST not only applies to manufacturers directly selling to the government, but to any subcontractor selling to a government supplier. And even if today you do not currently provide parts for any supplier serving the government, do you really want to count yourself out of any future opportunities to sell to a supplier who does serve the government?
Myth #3
"Becoming NIST compliant would take a long time. It's too late for us."
Not true. It’s faster and easier than you think. For most manufacturers, you can make significant progress down the path to NIST compliance within 30 days.
Many companies already have some of the technology in place required for NIST compliance, which can make the assessment less lengthy. In those cases, the assessment will focus on what process changes are needed to meet NIST compliance.
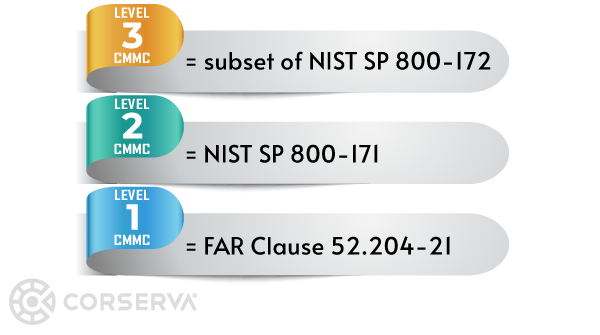
NIST 800-171 & CMMC
To increase the cybersecurity posture of companies operating in government supply chains, a new certification has been created, Cybersecurity Maturity Model Certification (CMMC).
Unlike NIST 800-171, CMMC has levels. Your method for CMMC compliance depends on the level of CMMC to which you need to comply. You may need an outside assessment or you may be able to self-attest to CMMC.
The Department of Defense is gradually transitioning from the NIST 800-171 mandate to the CMMC framework. By October 1, 2025, all new DoD contracts will require compliance with CMMC.
Benefits of Compliance
The good news for manufacturers who embark on the effort to meet the NIST 800-171 mandate or CMMC is that it provides a competitive advantage over manufacturers that have not.
Also, a side benefit of becoming compliant with NIST 800-171 and CMMC is that once you do, you have also made significant progress on the path to comply with NIST 800-53, another competitive advantage.
By complying with NIST 800‑171, you will also meet the majority of the criteria for NIST 800-53.
NIST Assessments
Corserva has been in business for over 30 years and offers a large portfolio of IT and consulting services. Our team has a very strong focus on IT security assessments, including assessments for NIST 800-171 and NIST 800-53.
 CMMC Readiness
CMMC Readiness
Corserva can prepare you for a CMMC assessment by a C3PAO or help you self-attest to CMMC.
Corserva is a CMMC-AB Registered Provider Organization™ (RPO) and we are listed on the CMMC-AB Marketplace.
As an RPO, Corserva is authorized by the CMMC-AB to provide pre-assessment consulting services to government contractors and other Organizations Seeking Certification (OSC).
Corserva has created an easy process to enable you to get ready for a CMMC assessment and protect your government contracts.
To prepare you for your CMMC assessment, these are the steps we follow:
- Identify the relevant requirements of CMMC you will need to meet.
- Perform an "as is" gap analysis of your processes and security controls, identifying areas to be corrected.
- Create a list of remediation steps to be taken prior to your certification assessment being performed by a C3PAO.
The end deliverable to you is a clear set of corrective actions to take before your CMMC assessment.
Get started today by requesting a quote.




