"Nation State Level Attacks" or "Zero Days" grab people’s attention (the hook), but if you are truly concerned about security (the line), your concerns should be more about the protection of logon credentials (the sinker).
Compromised logon credentials are the number one method used by attackers to gain access into systems they should not be in.
How Do Attackers Gain Access to Logon Credentials?
Attackers gain access to logon credentials in a number of ways. They include:
- Dictionary attacks and brute force
- Man in the middle attacks
- Sniffing
- Simply asking someone for their password
It is this last category, technically known as social engineering or phishing, that is the focus of this article. It is a technique where the attacker pretends to be someone or something that they are not. They gain the confidence of the victim and then simply ask them for their logon information.
Note: This technique is not restricted to logon information. Often the goal may instead be maiden names, account numbers, social security numbers, or some other piece of personally identifiable information (PII).
The following is a typical email phish that was recently brought to my attention. It clearly demonstrates an attempt to gain confidence by coming from a previously known associate and looking official. However, this one falls a bit short in its attempts, revealing a variety of telltale giveaways.
This real-life example of a phishing attack is an attempt to help you and your employees avoid becoming victims.
Anatomy of a Phishing Attack
A person receives an email from a "trusted" business associate. The subject line reads as follows.
FW: FYI
FLAG: Subject line is vague or ambiguous.
The body of the email reads:
Please see the attached document bellow for your reference.
FLAG: One word is misspelled, 'bellow,' which is not necessarily a significant flag but could be.
Attached to the email is a PDF document.
FLAG: The recipient was not expecting any documents from the sender.
The PDF file looks like this:
 FLAG: Dropbox? That doesn't make sense. Why Dropbox?
FLAG: Dropbox? That doesn't make sense. Why Dropbox?
Within this document is a link.
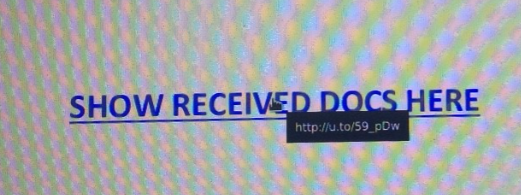
FLAG: The URL is odd. It's certainly not a Dropbox URL.
If you click on the URL, you are sent to this screen:
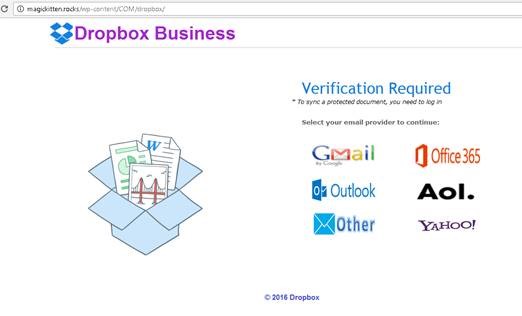
FLAG: The URL (magickittens.rocks) is different from the linked URL and is not a Dropbox URL.
If you click on any of the six email provider images, you see this login popup:
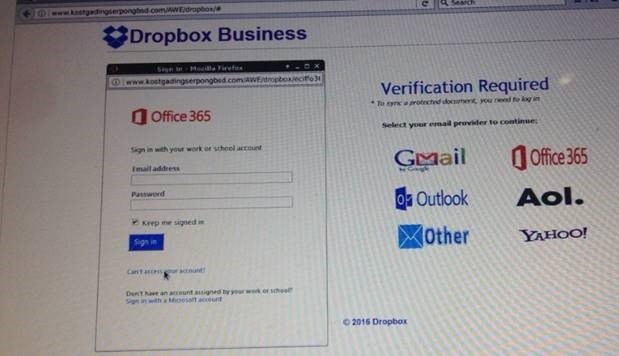
FLAGS:
- The login entry URL is not using HTTPS.
- The login entry URL is not for the service being logged into (Office 365).
- If you're logging into Dropbox, why isn't Dropbox one of the login options?
Once the user gives up their information and enters their email and password (no matter what they enter), they get to a real Dropbox login screen.
FLAG: If you've already entered your credentials to log in, why do you have to log in again?
Avoid Becoming a Victim
Anyone can be the target of hackers trying to gain access to systems and information. Sometime a phish is sent to a wide number of targets trying to catch a few. Other times the attacker targets a specific systems administrator or financial employee within the organization. This is known as Spear Phishing.
A variety of social engineering and phishing techniques are used as they attempt to extract information from their prey. You’re probably familiar with the phone scam where the caller tries to convince you to allow remote access to your computer. They claim they want to fix a virus; in fact, they are doing exactly the opposite. (“Hello, this is Microsoft technical support calling…”)
It is important for everyone to be aware of these deceptive practices. Be wary of links within emails. If those links take you to a logon page, be extremely careful. In fact, I recommend that instead of using such a link, perform a simple google search and log in to the destination site in that way.
Rely on Corserva for Cybersecurity Protection
Corserva provides managed IT security services as well as network security assessments and cybersecurity assessments. We design, develop, and deliver customized security solutions for you based on industry best practices.
Most engagements begin with an initial network security assessment to evaluate the current IT infrastructure. Your final secure network infrastructure will be the result of a team effort between Corserva and leaders from your IT and business operations departments.
Our goal is to create effective security solutions that are realistic and structured to your unique business needs. Contact us to learn more or to request a quote.




