You're sipping your morning coffee, about to dig into your ever-ample to-do list for the day, when you learn that a coworker’s Office 365 email account is compromised.
Many things flash through your mind, some of which can’t be shared in public, but predominantly it comes down to,
"What do we do now?"
Attacker Sends Phishing Emails from Compromised Account
In this type of email compromise, the attacker has uncovered your user's Office 365 account credentials and has been accessing the user's mailbox.
The attacker then often sends emails out from that account with two goals in mind:
- Seeking financial gain
- Compromising the accounts of additional people for the purpose of extending the attacker's realm of control
Perform Email Forensics
In the event of a compromise, there are two things that should be done immediately and simultaneously from within the Office 365 Admin Center portal:
 Reset the user’s password.
Reset the user’s password.- Sign the user out of all Office 365 sessions.
While a recent change made by Microsoft regarding Continuous Access Evaluation has lessened the need for step 2, I still recommend that it be done.
With these two steps, you have prevented the attacker from logging into the account again while also disconnecting the attacker from all existing connections to Office 365.
Determine the Level of Access
If the compromised user has Administrator rights within your Office 365 tenancy, your forensic and recovery procedures are beyond what this article discusses.
 With Administrative rights, it is possible the attacker has already taken steps to maintain persistence in the environment. The attacker can regain access anytime after the initial account compromise is detected and resolved. A much more thorough analysis of your environment should be done. I recommend you consider engaging a professional service provider for assistance.
With Administrative rights, it is possible the attacker has already taken steps to maintain persistence in the environment. The attacker can regain access anytime after the initial account compromise is detected and resolved. A much more thorough analysis of your environment should be done. I recommend you consider engaging a professional service provider for assistance.Remove Rules in the Account
In these types of email compromise attacks, it is extremely common for the attacker to create mailbox rules to automatically forward emails. This is done in an attempt to prevent the real account owner from noticing their account has been compromised.
Rules created by the attacker search for email messages meeting these types of conditions:
- The subject or body contains words such as "hacked" or "compromised"
- Sender's email is (for example) initialphish@email.com
Any emails meeting the criteria are moved to Junk, RSS, or another subfolder within the user's mailbox, which are commonly off the radar of typical users yet still accessible by the attacker.
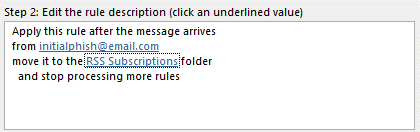
Look for similar rules that, in effect, result in moved or deleted emails, and remove these rules.
Enable Office 365 Auditing
In order to identify attackers and dig deeper into what and when things happen in Office 365, it is important that activity auditing be enabled.
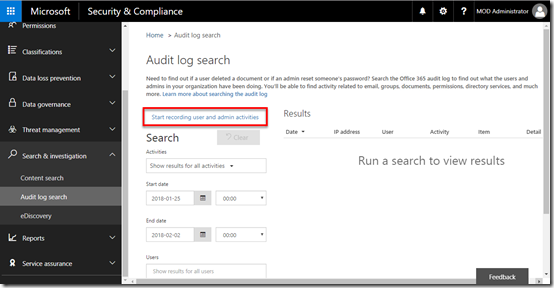
Recently, Microsoft has enabled activity auditing by default for all Office 365 customers. If you have had Office 365 for some time, you should verify it is enabled.
Identify the Attacker
In the case of email compromise, it is nearly impossible for you to truly identify the attacker as an individual person. You can take steps to isolate from where the attack came from, and there are tools you can use to identify logs and emails related to the attack.
The most common way to (try to) identify the attacker is to perform an Audit Log Search on the compromised user’s email address.
Within the results from the Audit Log Search on the compromised user's account:
- Look for user logged-in events.
- Sort on IP address.
- Remove all known IP addresses coming from your office and remote office users.
Hopefully, you will be left with a much smaller subset of IP addresses to review.
By running the remaining IP addresses through an IP address geolocation lookup, you may be able to identify where the attacker’s logins came from.
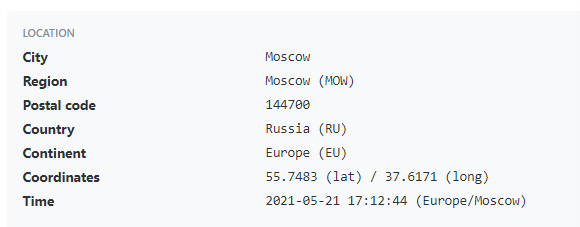
Keep in mind that depending on how long an attacker was in the mailbox, the IP address could change from day to day.
Back Track to Determine What Happened
Once you have identified the attacker's source IP addresses, you can feed these back into the Audit Log Search tool. This will usually result in a substantial number of results.
You can export the list of IP addresses to a .csv file, then import it into your favorite data analysis tool to review. This should provide great insight into when the initial login occurred to gain control of the account, rules that were used, and time periods to focus on regarding emails that may have been sent.
Warn Others Whose Accounts May Have Been Compromised
If you don't already have a properly configured secure email gateway, which would very likely prevent the mass mailing of outbound emails, you should now consider contacting any clients that were sent phishing emails from the compromised account. This way, you can protect your company’s reputation and help others quickly identify any possible compromised accounts and stop the spread.
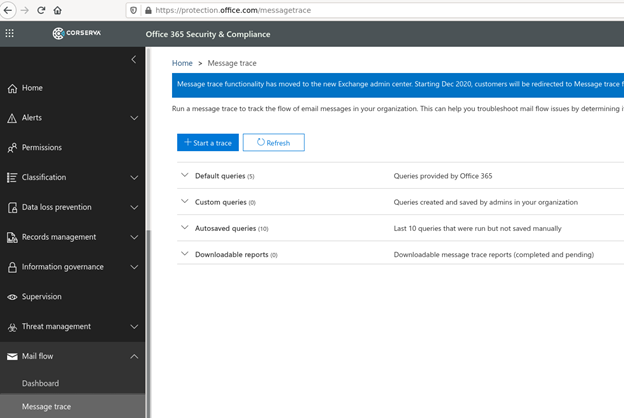
To determine the extent of the damage outside your organization, you can use message traces that look for emails sent during a specific time period and initiated from known bad IP addresses.
Prevent an Email Compromise
When working with a client to investigate an email compromise, I like to address the root cause of such issues and how future compromises can be prevented once the immediate impact has been resolved.
- Enable multi-factor authentication (MFA) on all Office 365 user accounts, especially those with admin privileges.
- Provide security awareness training to users, which will train people how to identify phishing emails.
- Instruct users in security best practices such as never reusing passwords.
- Implement a secure email gateway solution that lessens the impact of email compromise attacks in two ways: preventing the initial phishing email from ever coming in and stopping any subsequent email floods from going out.
Corserva's Cybersecurity Services
Hopefully, you will rarely find yourself in the position of having to analyze an email attack forensically. If you do, I hope this article was helpful.
If you would like assistance in either the event of an email compromise or in taking proactive steps to prevent one, please contact Corserva. We provide cybersecurity services that enable our clients to efficiently prevent intrusions and recover from security breaches. Our services include managed SIEM, email security, managed firewall, patch management, security awareness training, and more.